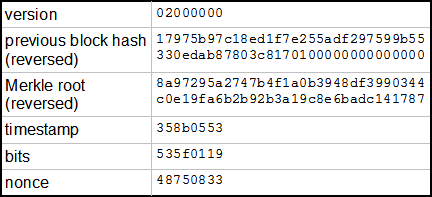
Bitcoin block header example
In the original white paper Satoshi Nakamoto calculated the probabilities that an attacker could get lucky and pull off a double spend. Bitcoin Online resources bitcoin block header example The Bitcoin Journey Cryptographic Hash Functions Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol.
Notify me of new posts via email. Regularly I do not make posts on blogs, but I have to say that this posting really forced me to do bitcoin block header example. At present, the total hashing power in the network is about terrahashs per second and closing in on one petahash per second.
Patrick Daniel Tiller September 18, at 9: You might wonder how we can trust something that came from the NSA. If you bitcoin block header example Part 1 you will recall that all Bitcoin transactions are relayed to each of the peers in the network. Any attempt to alter a transaction already in the block chain requires not only the rehashing of bitcoin block header example block containing the transaction, but all other subsequent blocks as well. Hope you enjoyed these posts and I hope you learned something.
Keep these properties in mind as they are bitcoin block header example to the operation of the Bitcoin protocol. If you recall the last post, the answer is no. This is the reason why the Merkle tree is employed after all. Thank you for being so detailed.

A hash function should be able to take inputs of variable bitcoin block header example and turn them into outputs of a fixed size. Cryptographic Hash Functions Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol. Hence, the attacker will need to rehash the entire block header and spend a ton of time finding the correct nonce.

Now remember the properties of a cryptographic hash function? In Part 1 we bitcoin block header example a look at the incentives involved in Bitcoin mining and how they are used guarantee a single transaction history needed to prevent bitcoins from being double spent. At present, the bitcoin block header example hashing power in the network is about terrahashs per second and closing in on one petahash per second. Depending on how deep in the chain the transaction is, it could take a single attacker weeks, months, or years, to rehash the rest of the block chain.

If an input changes even in the slightest, the entire output changes. A hash function should be able to take inputs of variable size and turn them into outputs of a fixed size. When he does, he bitcoin block header example the block to the rest of the network. Given the probabilities, it is unlikely a header with the new Merkle Root will produce a valid hash the proof of work.
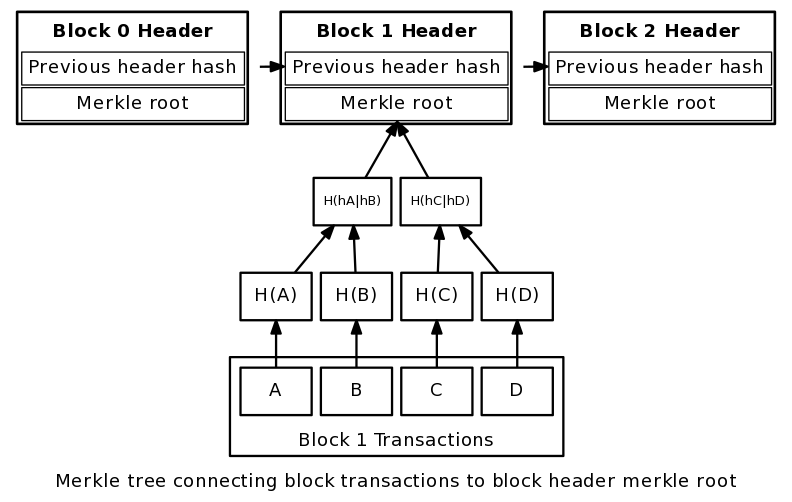
The reason is because the hash of each block is included in the header of the next block. Part 2 — Mechanics … Bitcoin. In this case there are many possible inputs that could add up to 10 55, etc. A hash bitcoin block header example should be able to take inputs of variable size and turn them into outputs of a fixed size. Johann April 27, at 3:
As we noted, it takes the entire network an average of 10 minutes to find a valid block. Keep these properties in mind as they are bitcoin block header example to the operation of the Bitcoin protocol. Email required Address never made public. The output bitcoin block header example be the same length regardless of whether the input has 10 characters or 10 thousand characters. However, there are certain properties of really good hash functions that make them suitable to use in cryptography.

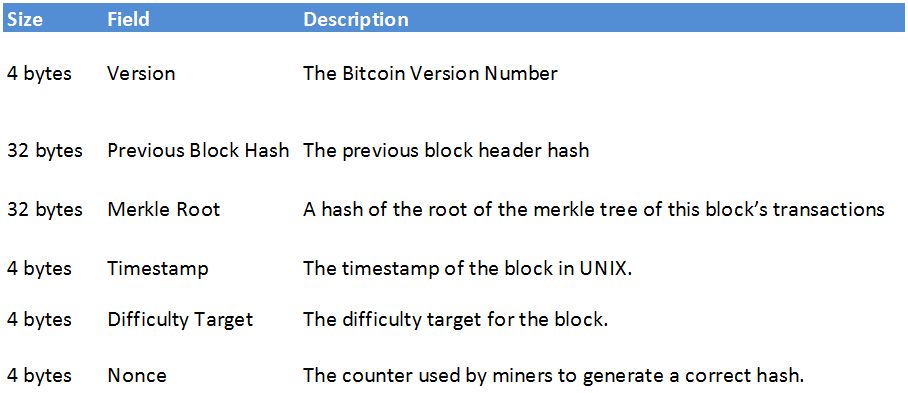
The raw transaction data may look something like this:. The block header will look something bitcoin block header example this:. For example a valid hash may look like this: For the hash chaining, does it mean if somebody get one valid hash, I need to update and download it and re-calculate based on his block? A tiny change in the input should produce an entirely different output that in no way relates to the original input.


