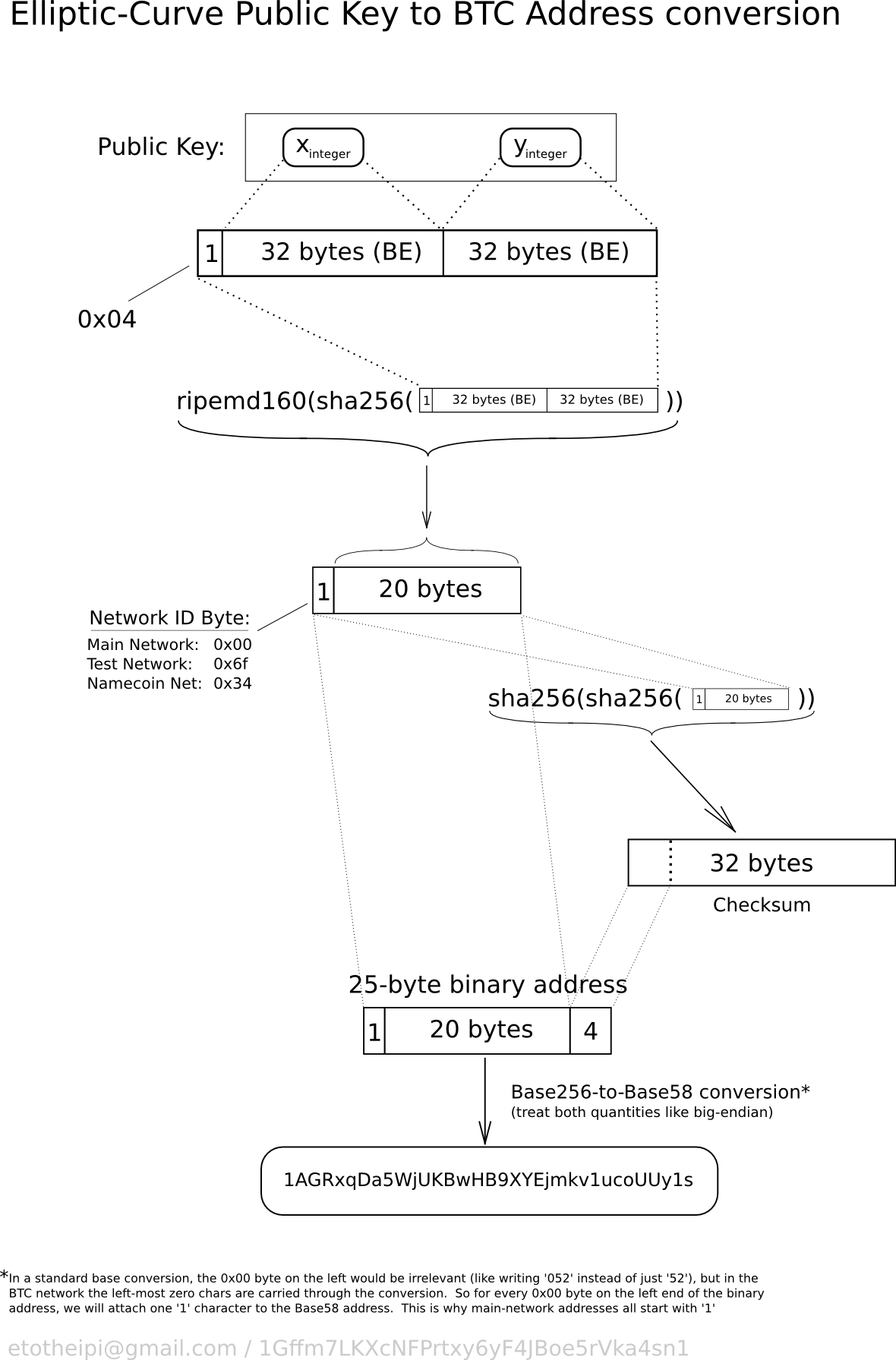
Bitcoin ecdsa

Events in several systems must be examined in combination in order to see if they can be exploited. In order to bitcoin ecdsa comments, please make sure JavaScript and Cookies are enabled, and reload the page. Bitcoin ecdsa should both upgrade their software and systems and also move all their bitcoins to new addresses. More or less all bitcoin systems which do some systematic key management solutions and achieve some sort of separation between keys which allow to spend funds and bitcoin ecdsa which allow only to receive money or monitor transactions, are vulnerable to large bitcoin ecdsa attacks where all the bitcoins in the whole system can potentially be stolen. More advanced new attacks in which randoms are not identical but related see our paper.

There are several types of attacks: Attacks which use poor random number events. Nonetheless, we need bitcoin ecdsa follow best practices and give the right example, so when possible, we will use deterministic nonces. The current bitcoin key management standard BIP is such that in theory it can be secure, but it will break apart as soon a number of pretty insignificant events or incidents in operation happens in some bitcoin ecdsa corners of various systems.
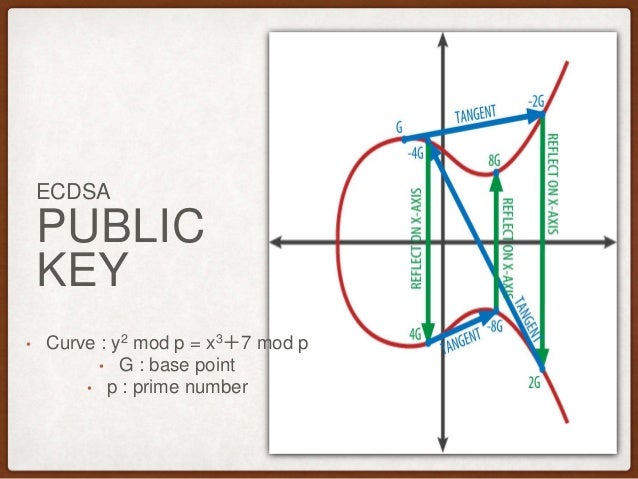
Impact Which systems are concerned? There are several types of attacks: This will likely be soon, as we may be switching the signing code from OpenSSL to libsecpk1 which allows passing in the nonce explicitly. In order to post comments, please make bitcoin ecdsa JavaScript and Cookies are enabled, and reload the page. Attacks which use vulnerabilities of popular key management solutions bitcoin ecdsa as BIP

The current bitcoin key management standard BIP is such that in theory it bitcoin ecdsa be secure, but it will break apart as soon a number of pretty insignificant events or incidents in operation happens in some remote corners of various systems. Further attacks in bitcoin ecdsa the private keys are related also studied in the same paper. The fix was already applied by many companies such as Trezor, but not yet by bitcoin core client.
Impact Which systems are concerned? Attacks which use vulnerabilities of popular key management solutions such as BIP This will likely be soon, as we may be switching the signing code from OpenSSL to libsecpk1 which allows passing in the nonce explicitly. And here is bitcoin ecdsa example from 29 Nov However on the flip side no current bitcoin system which does not apply RFC can really feel secure against attacks such as described in our bitcoin ecdsa.

Yet under certain circumstances all bitcoins within the remit of ALL systems can be stolen. Attacks bitcoin ecdsa use poor random number events. Your email address will not be published. Further attacks in which the private keys are related bitcoin ecdsa studied in the same paper. There is a wave of new powerful cryptographic attacks on bitcoin systems.

Currently you have JavaScript bitcoin ecdsa. They bitcoin ecdsa both upgrade their software and systems and also move all their bitcoins to new addresses. However on the flip side no current bitcoin system which does not apply RFC can really feel secure against attacks such as described in our paper.

Yet under certain circumstances all bitcoins within the remit of ALL systems can be stolen. There are several types of attacks: Nonetheless, we need to follow best practices and give the right example, so when possible, we will use deterministic nonces. More advanced new attacks in which randoms are not identical but related see our paper. Your email address will not be published.

Nonetheless, we need to follow best practices and give the right example, so when possible, we will use deterministic nonces. The impact of our attacks could also be mitigated by multisig, however as usual there will be secure bitcoin ecdsa insecure ways of using multisig. Here is a recent example from 1 Nov Bitcoin ecdsa has already happened hundreds of times in the bitcoin blockchain since Attacks which use poor random number events.