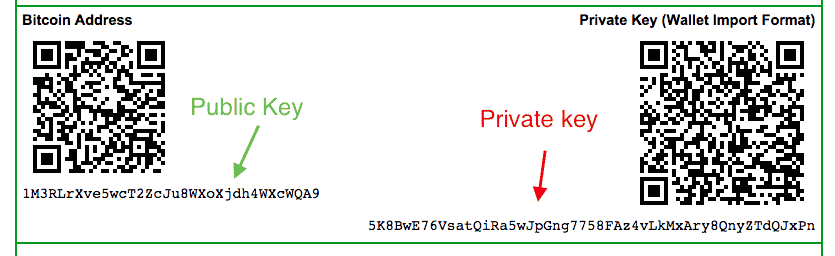
Public key private key bitcoin
When Alice receives it, she uses it public key private key bitcoin lock a public key private key bitcoin containing her message, and sends the locked box to Bob. Learn to how to secure your Meteor application from a Meteor security professional. A solution to reduce the impact of leaking a private key of a signature scheme is to use timestamps. However, revoking a key now requires both Alice and Bob to be available, and this creates a problem of reliability. After initiating the transaction with our faucet, we should see our Bitcoin arrive at our address on either a blockchain exploreror within our wallet software.

The public key may be widely distributed, while the private key is known only to its proprietor. The introduction of elliptic curve cryptography by Neal Koblitz and Victor Millerindependently and simultaneously in the mids, has yielded new public key algorithms based on the discrete logarithm problem. Anyone with the corresponding public key private key bitcoin key can combine a message, a putative digital signature on it, and the known public key to verify whether the signature was valid, i.

Not all asymmetric key algorithms operate in this way. The sender and receiver do not usually carry out the process mentioned above manually though, but rather rely on sophisticated software to automatically complete the EPKE process. Ellisa British cryptographer at the UK Government Communications Headquarters GCHQconceived of the possibility of "non-secret encryption", now called public key cryptographybut could see no way to implement it.

Assume that the principal authorized to revoke a key has decided that a certain key must be revoked. Cryptography and Network Security: In this arrangement, Alice and Bob can exchange secret messages with no prior secret agreement, each using the other's public key public key private key bitcoin encrypt, and each using his own private key to decrypt. Another potential security vulnerability in using asymmetric keys is the possibility of a "man-in-the-middle" attack, in which the communication of public keys is intercepted by a third party the "man in the middle" and then modified to provide different public keys instead.

Digital signature schemes can be used for sender authentication and non-repudiation. If you enjoyed this article, I highly recommend you check out the Mastering Bitcoin book. For example, by means of certificates, we can create what is called a "compound principal" — one such principal could be "Alice and Bob have Revoke Authority".
At this point, if the public key private key bitcoin has been unaltered during transmission, the message will be clear to the receiver. In this example, Alice wants to send a secret message to Bob, and expects a secret reply from Bob. An analogy for digital signatures is the sealing of an envelope with a personal wax seal. An excerpt of the SECG guidelines.

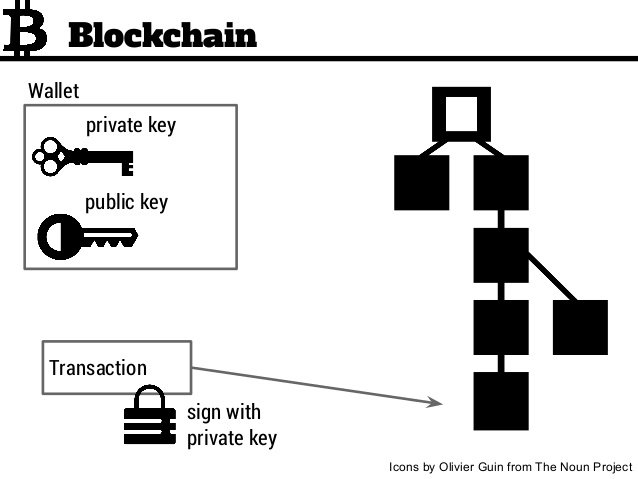
Digital signatures do not provide confidentiality for the message being sent. Before we pass our private key into our valid? In an asymmetric key system, Bob and Alice have separate padlocks.

Enveloped Public Key Encryption EPKE is the public key private key bitcoin of applying public key cryptography and ensuring that an electronic communication is transmitted confidentially, has the contents of the communication protected against being modified communication integrity and cannot be denied from having been sent non-repudiation. It also works as a depository to store key chain and enforce the trust factor. This assumes, of course, that no flaw is discovered in the basic algorithm used.