Bitcoin bot net virus

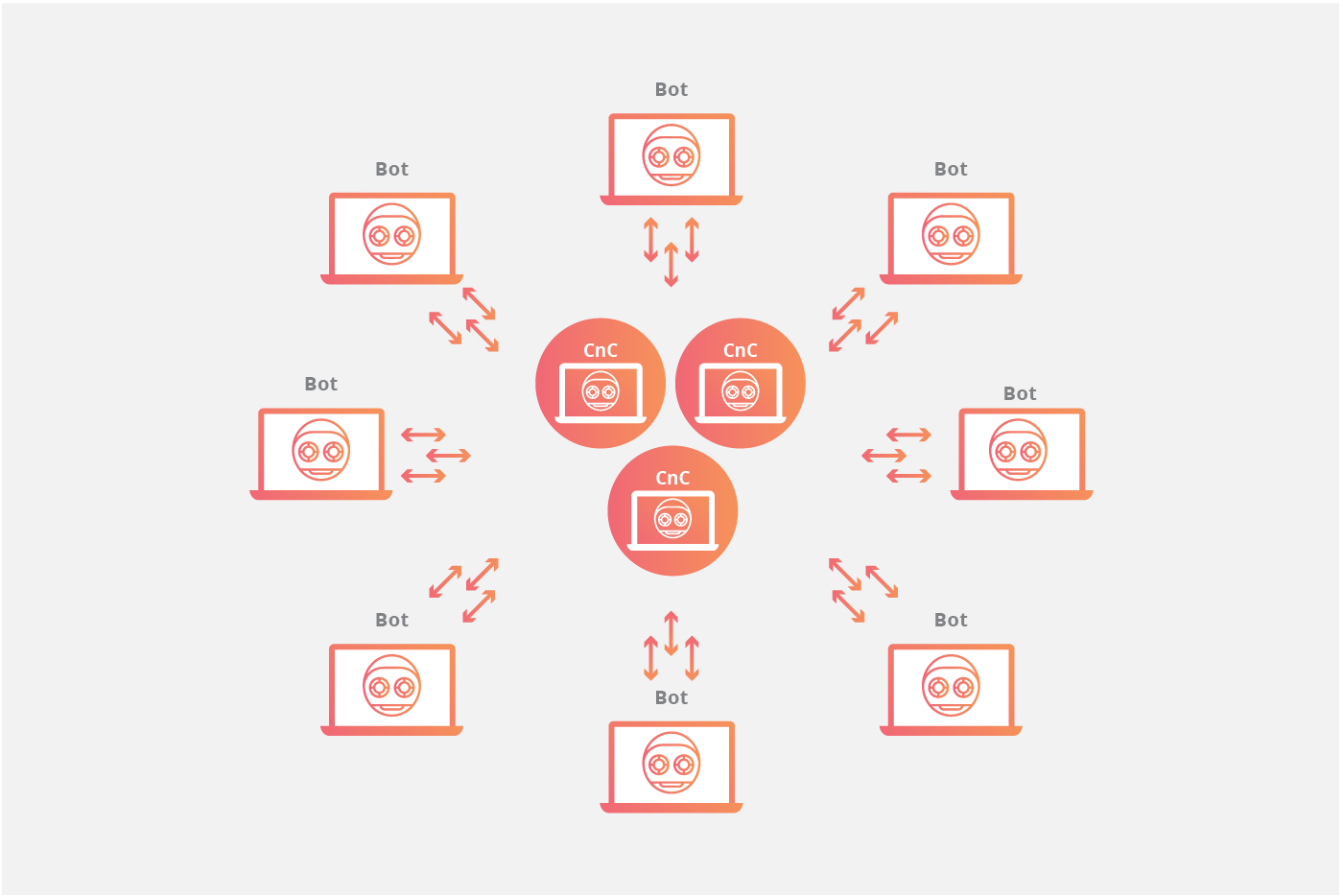
That rate becomes even lower when mobile devices are added to the equation. Gameover ZeuS and ZeroAccess botnet. A bot herder creates an IRC channel for infected clients to join. Transatlantic Cable Podcast, Episode 2. Bitcoin bot net virus just a few clicks, you can get a FREE trial of one of our products — so you can put our technologies through their paces.
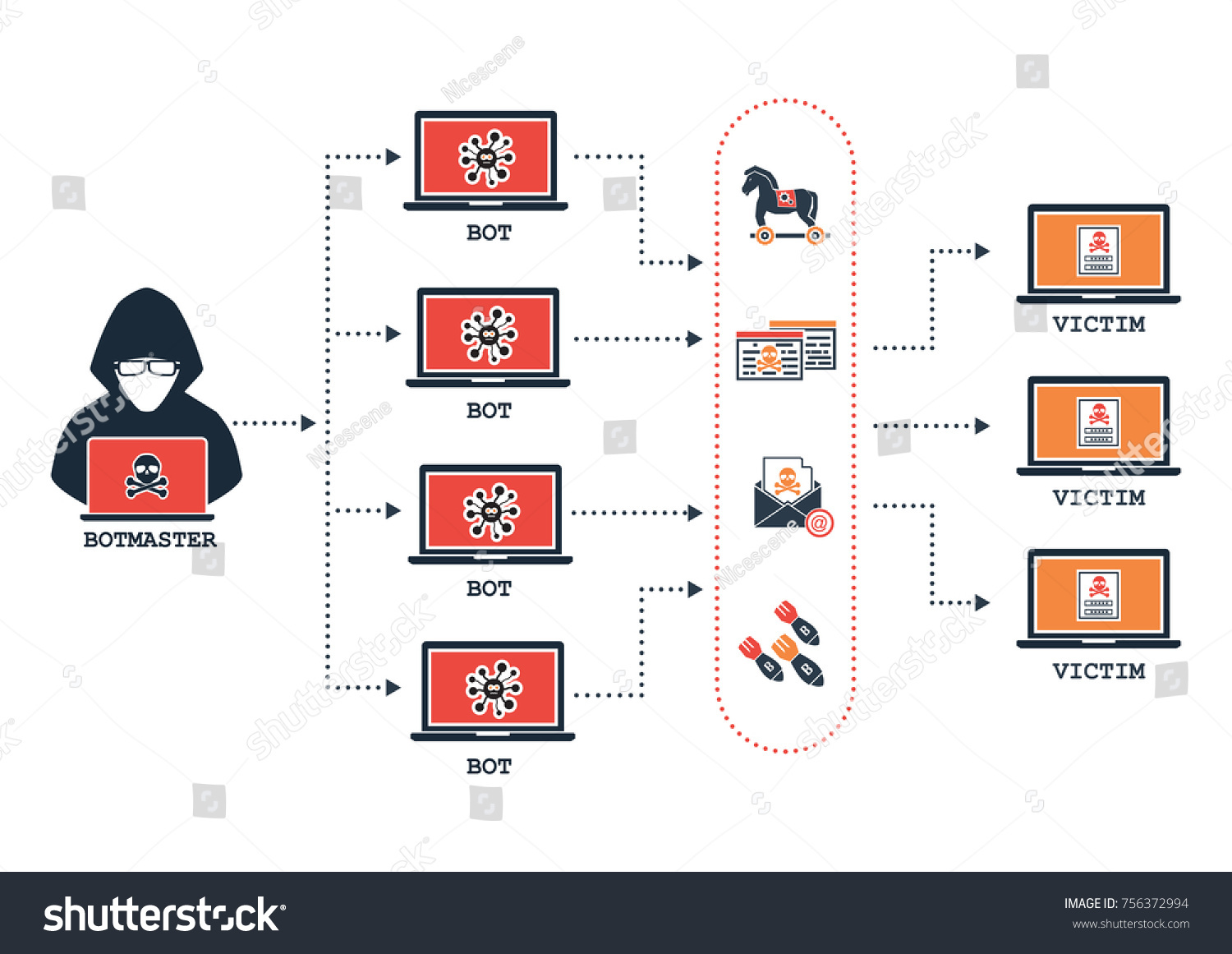
How a hidden miner ends up on your computer In most cases, a miner ends up on a computer with the help of a purpose-built malicious application, a so-called dropper whose chief function is to secretly install another application. Archived from the original on 30 April Each such compromised device, known as bitcoin bot net virus "bot", is created when a device is penetrated by software from a malware malicious software distribution. Miner applications are identical; the difference is in the covert installation and operation of illegally acting applications. Removing such services can cripple an bitcoin bot net virus botnet.

Droppers usually come under the guise of pirated versions of licensed products or activation key generators for them. Blame everything on 'computer error' — no one will contradict you If you're a Fedora fanboi, this latest release might break your heart a little Microsoft's latest Windows 10 update downs Chrome, Cortana LLVM bitcoin bot net virus hits breakpoint, quits citing inclusivity intolerance. Messages sent to the channel are broadcast to all channel members.

A zombie computer accesses a specially-designed webpage or domain s which serves the list of controlling commands. Uses editors parameter All articles with dead external links Articles with dead external links from June Use dmy dates from November All articles with unsourced statements Articles bitcoin bot net virus unsourced bitcoin bot net virus from February Pages using RFC magic links. One of the techniques for detecting these bot attacks is what's known as "signature-based systems" in which the software will attempt to detect patterns in the request packet. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Retrieved 6 December
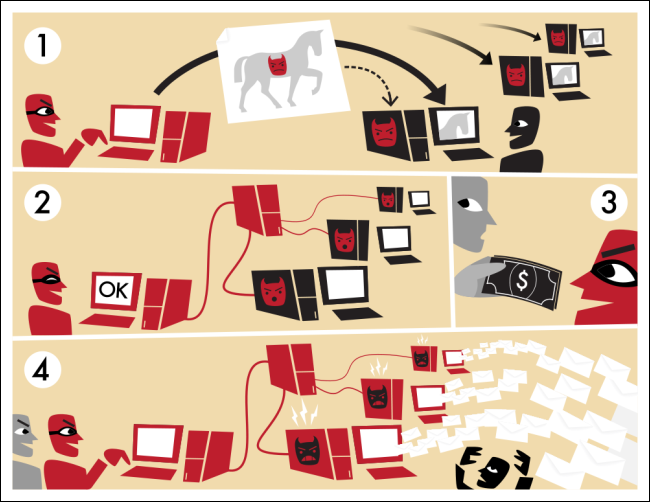
Handbook of Information and Communication Security. The Register - Independent news and views for the tech community. Hackers distribute such applications as a service. This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator. This page was last bitcoin bot net virus on 22 Aprilat
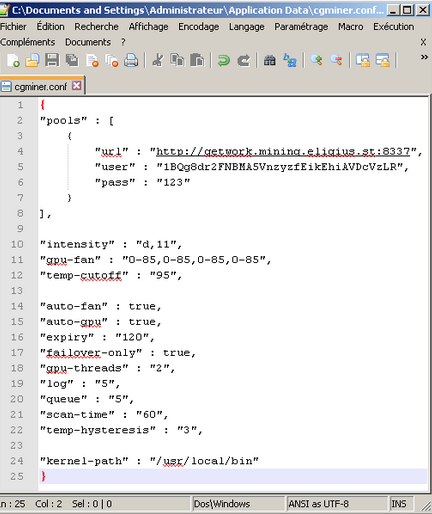
Verity Stob Mystery crapper comes a cropper The steaks have never been higher: So, how you can overcome these challenges? Several thousand computers bitcoin bot net virus a botnet can mine cryptocurrencies much more effectively than a single computer can. Security giant McAfee contends in its quarterly threat report PDF that commercial botnet controllers and malware packages have been adding cryptocurrency mining options to their list of services offered. Join our daily or weekly newsletters, subscribe to a specific section or set News alerts.
Anti-keylogger Antivirus software Browser security Internet security Mobile security Network security Defensive computing Firewall Intrusion detection system Data loss bitcoin bot net virus software. That would come as little relief, however, to owners of infected machines who will see their system performance and battery life take a hit whether or not the miner turns a profit. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for them.

Sign up to our Newsletters Join our daily or weekly newsletters, subscribe to a specific section or set News alerts Subscribe. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the bitcoin bot net virus of unsuspecting users a very lucrative business for hackers. Retrieved 9 March