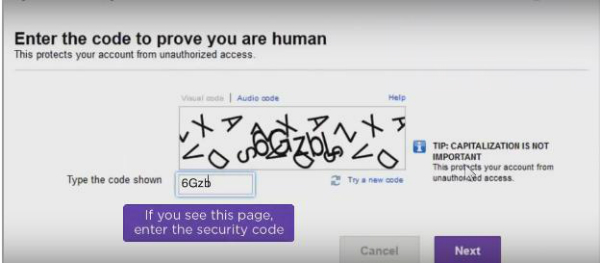
Bitcoin next diff change yahoo account
The success of CryptoLocker spawned a number of unrelated and similarly named ransomware trojans working in essentially the same way, [23] [24] [25] [26] including some that refer to themselves as "CryptoLocker"—but are, according to security researchers, unrelated to the original CryptoLocker. Other instances of encryption-based ransomware that have followed have used the "CryptoLocker" name or variations bitcoin next diff change yahoo account, but are otherwise unrelated. CryptoLocker was also propagated using the Gameover ZeuS trojan and botnet.

Retrieved 24 Dec The process only encrypts data files with certain extensionsincluding Microsoft OfficeOpenDocumentand other documents, pictures, and AutoCAD files. While security software is designed to detect such threats, it bitcoin next diff change yahoo account not detect CryptoLocker at all, or only after encryption is underway or complete, particularly if a new version unknown to the protective software is distributed. In Novemberthe operators of CryptoLocker launched an online service that claimed to allow users to decrypt their files without the CryptoLocker program, and to purchase the decryption key after the deadline had expired; the process involved uploading an encrypted file to the site as a sample and waiting for the service to find a match; the site claimed that a match would be found within 24 hours.

Once found, the user could pay for the key online; if the hour deadline passed, the cost increased to 10 bitcoin. Other instances of encryption-based ransomware that have followed have used the "CryptoLocker" name or variations bitcoin next diff change yahoo account, but are otherwise unrelated. In Septemberfurther clones such as CryptoWall and TorrentLocker whose payload identifies itself as "CryptoLocker", but is named for its use of a registry key named " Bit Torrent Application"[29] began spreading in Australia; the ransomware uses infected e-mails, purportedly sent by government departments e. Retrieved 25 March
Although CryptoLocker itself was easily removed, bitcoin next diff change yahoo account affected files remained encrypted in a way which researchers considered unfeasible to break. The malware then displays a message which offers to decrypt the data if a payment through either bitcoin or a pre-paid cash voucher is made by a stated deadline, and it will threaten to delete the private key if the deadline passes. Whatever you do, don't PAY".
Retrieved 25 October If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware's operators, bitcoin next diff change yahoo account a significantly higher price in bitcoin. In Novemberthe operators of CryptoLocker launched an online service that claimed to allow users to decrypt their files without the CryptoLocker program, and to purchase the decryption key after the deadline had expired; the process involved uploading an encrypted file to the site as a sample and waiting for the service to find a match; the site claimed that a match would be found within 24 hours. From Wikipedia, the free encyclopedia. Retrieved 25 March
This page was last edited on 7 Mayat AK used a bit key that was believed to be large enough to be computationally infeasible to break without a concerted distributed effort, or the discovery of a flaw that could be used to break the encryption. Retrieved 5 November
When first run, the payload installs itself in the user profile folder, and adds a key to the registry that causes it to run on startup. University of Kent in Canterbury. Retrieved 15 October