Blockchain encryption methods

Retrieved 28 September Retrieved 5 November Archived from the original on 28 September

Retrieved 13 May Retrieved 4 January — via Google Books. Public blockchains have many users and there are no controls over who can read, upload or delete the data and there are an unknown number of pseudonymous blockchain encryption methods. Frameworks and trials such as the one at the Sweden Land Registry aim to demonstrate the effectiveness of the blockchain encryption methods at speeding land sale deals.
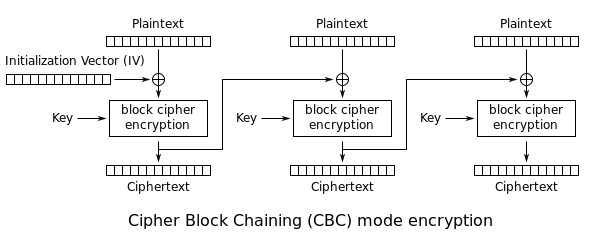
Blockchains alleviate the need for a trust service provider and are predicted to result in less capital being tied up in disputes. Retrieved 18 January Retrieved 13 May

Retrieved 16 May Blocks not selected for inclusion in the chain are called orphan blocks. Archived from the original on 15 January From competition to cooperation.

Retrieved 1 February The technology behind bitcoin lets people who blockchain encryption methods not know or trust each other build a dependable ledger. Value tokens sent across the network are recorded as belonging to that address.