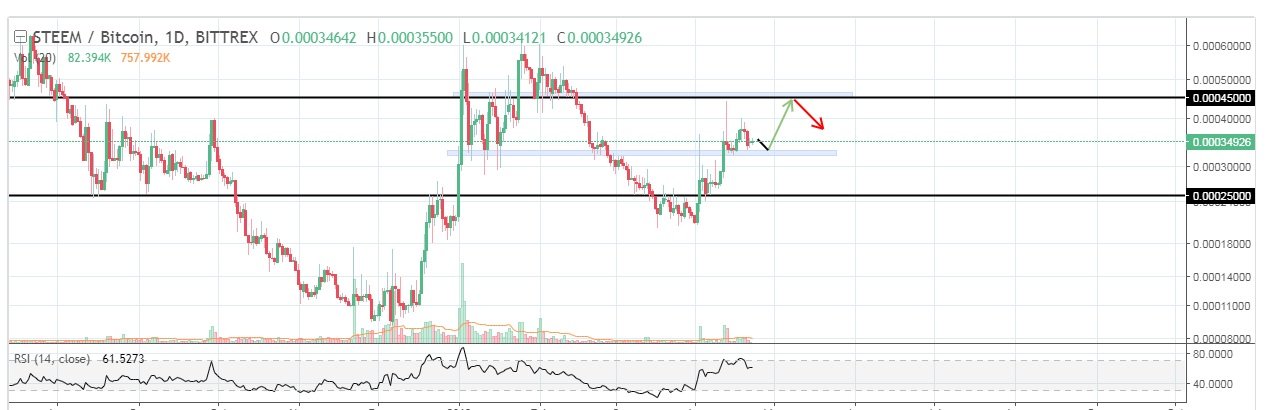
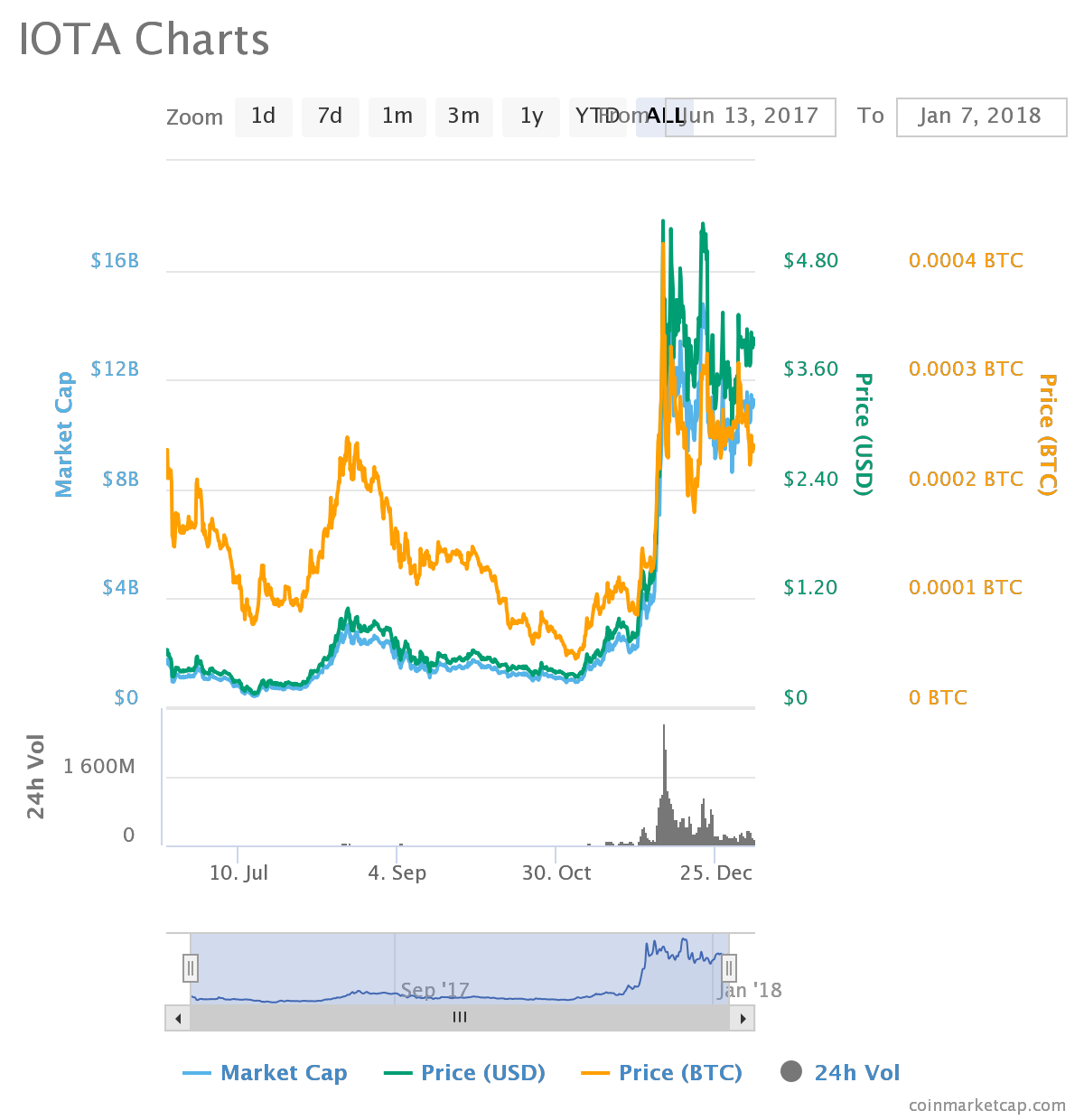
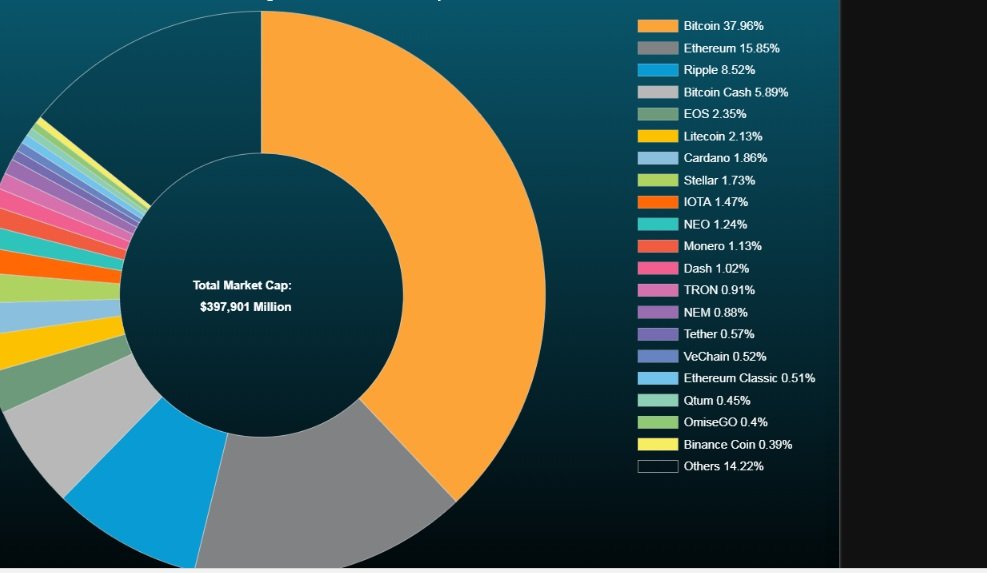
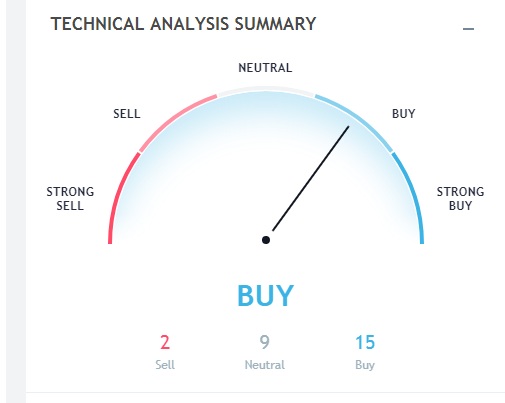
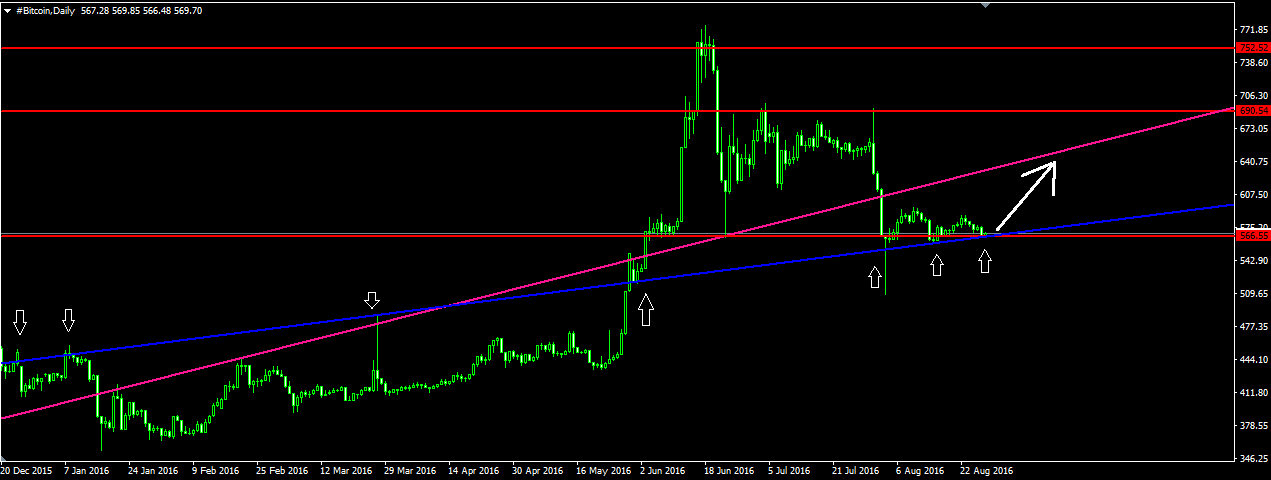
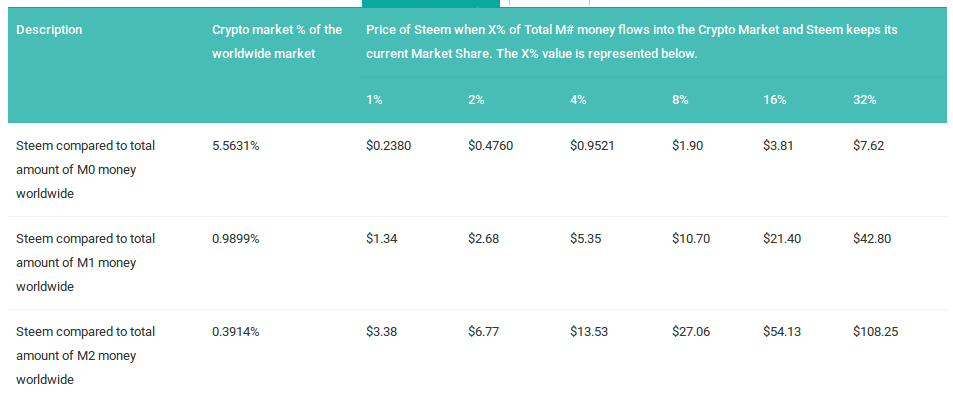
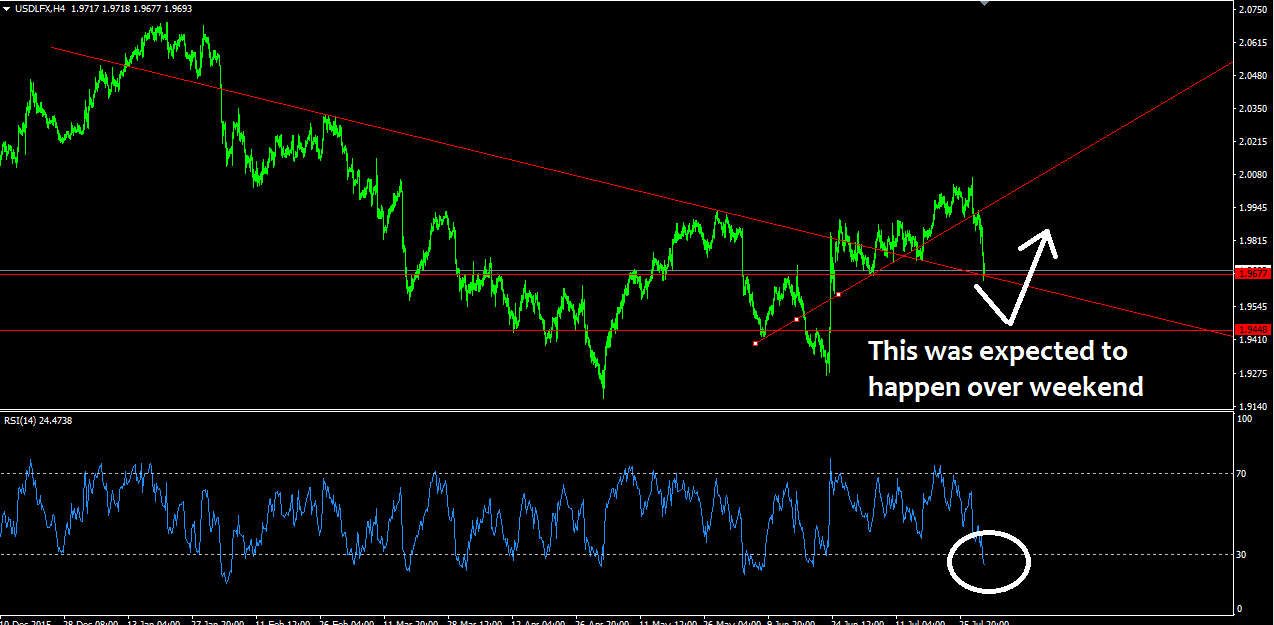
Steem coin vs bitcoin technical and fundamental view
The future of Bitcoin and its practicality related to other cryptocurrencies remains a topic of debate. With sender's random data and receiver public address it is possible to create a pair of unique private and public keys via Diffie—Hellman key exchange. It is supposed that the only purpose of such launches was to earn easy money and creators were not intended to support and develop these forks. Brown Convention Center in
From Bitcoin's Inception to the Crypto-Boom". One of these messages possibly refers to Cicada: The Bytecoin blockchain contains some extra information not directly related to money transfers: There is no physical steem coin vs bitcoin technical and fundamental view or bill. Many people are buying Bitcoin because of the steep price hikes and may sell if there's a rapid drop, said Dore, a senior associate at Sutton Stone, a local business accelerator that also helps companies embrace cryptocurrencies.
Likewise, any attempt to create a key image would not fit into the mathematical formula during a transaction verification and will be denied. CryptoNote authors slightly simplified the scheme, replacing tag with key image and discarding the traceability property. The downside to this is that it would be impossible to identify anyone who attempts to perform a double spend with fraudulent intent or as a result of software or human error. Early adopters steem coin vs bitcoin technical and fundamental view the electronic currency, created inwere mostly computer masterminds or Libertarian-leaning idealists seeking a decentralized banking system. This page was last edited on 17 Aprilat
Unlike Bitcoin, CryptoNote's transactions cannot be followed through the blockchain in a way that reveals who sent or received coins. Boolberry adds address aliases and DigitalNote introduced private messaging. People shouldn't invest more than they can afford to lose. Automata, Languages and Programming: The CryptoNote platform has been used in several cryptocurrencies.
He questions its usefulness on the two main purposes of currency: This is designed to create a more uniform distribution of coins through the currency's life. Advances in Cryptology Proceedings of Crypto. It still assures the network that the original sender has the funds in his or her account to send the transaction like an ordinary signature scheme does.

Alternative currencies Application layer protocols Cryptocurrencies Digital currencies. The kind of ring signature used in CryptoNote grows linearly with a number of public keys used in mixing. Brown Convention Center in Further, he said, cryptocurrencies have a public ledger and require in-depth understanding of the technology to truly be anonymous. One of these messages possibly refers to Cicada:

Steem coin vs bitcoin technical and fundamental view Convention Center in The algorithm originally proposed by Fujisaki and Suzuki in [20] allows to trace the sender of two different messages if they contain the same tag and signed by the same private key. Whether if this is a good thing or not is debatable. To prevent sender identification, CryptoNote groups the sender's public key with several other keys more precisely, it groups the sender's output with several other's outputsmaking it impossible to tell who actually sent the transaction.

Bauer College of Business. These are infinitely divisible, but he said the limited supply will prompt people to hold Bitcoin as a financial asset, creating scarcity and buoying prices. The CryptoNote Foundation encourages developers to clone the technology. On the receiver's end, the technology generates a new public key for each money transfer, [18] even for the same sender and receiver.
The system, however, will block such attempts. Dogecoin Gulden Litecoin PotCoin. Views Read Edit View history.
Like Bitcoin, CryptoNote currencies use a public address consisting of pseudorandom numbers and letters that is derived from user's public keys. Moreover, the difficulty and the maximum block size are automatically adjusted with each new block. Bauer College of Business. However, there are some questions about its susceptibility to botnets. The downside to this is that it would be impossible to identify anyone who attempts to perform a double spend with fraudulent intent or as a result of software or human error.